Purpose of this post
This cheat sheet is the main resource coming in with me into my CAB441 Network Security exam. As we have access to the internet, it was encouraged to create a sheet that would be readily accessible and CTRL-F-able.
Perl nikto.pl -h 192.168.1.188 -Cgidirs all -o test -Format csv The 'all' options would instruct Nikto2 to test all available CGI directories. If you want to specify a specific CGI directory, the. Home Instant Answers Nikto Cheat Sheet Next Steps. This is the home page for your Instant Answer and can be. Tools Cheat Sheet. Bug Bounty & Pen-Test Templates. Powered by GitBook. Nikto # To scan a particular host. Nikto -host host IP/name # To scan a host on multiple ports (default = 80) nikto -host host IP/name -port port number 1, port number 2, port number 3. Nikto Cheat Sheet Infographic. September 27, 2018 Admin. Below is a helpful infographic for basic commands and usage with the tool Nikto. Tutorials cheat sheet.
Network Security
Iptables
Here’s a coolcheat sheet. man iptables and main iptables-extensions are both very useful. If you want to visualise your iptables rules,check this out.
Chains
There are five built in iptables chains.
- INPUT
- OUTPUT
- FORWARD
- PREROUTING
- POSTROUTING
Tables
There are five built-in iptables tables. The first three are the most common. The following descriptions have been taken from the TABLES section of the man pages. The previous flow chart also shows the different tables.
filter
This is the default table (if no -t option is passed). It contains the built-in chains INPUT (for packets destined to local sockets), FORWARD (for packets being routed through the box), and OUTPUT (for locally-generated packets).
nat
This table is consulted when a packet that creates a new connection is encountered. It consists of four built-ins: PREROUTING (for altering packets as soon as they come in), INPUT (for altering packets destined for local sockets), OUTPUT (for altering locally-generated packets before routing), and POSTROUTING (for altering packets as they are about to go out).
mangle
This table is used for specialized packet alteration. Until kernel 2.4.17 it had two built-in chains: PREROUTING (for altering incoming packets before routing) and OUTPUT (for altering locally-generated packets before routing). Since kernel 2.4.18, three other built-in chains are also supported: INPUT (for packets coming into the box itself), FORWARD (for altering packets being routed through the box), and POSTROUTING (for altering packets as they are about to go out).
There are also raw and security tables.
Targets
There are six iptables targets.
- ACCEPT
Let the packet through.
- DROP
Drop the packet on the floor
- REJECT
Let the other end know the destination port is unreachable
- MASQUERADE
Mask the private IP address of a node with the exernal IP address of the firewall / gateway
- RETURN
Stop traversing the chain and resume at the next rule in the previous (calling) chain. If the end of the chain is reached, the chain policy is used.
- QUEUE
Pass the packet to userspace
Note: there are more targets that have very specific cases. For example, the DNAT target can only exist in the nat table and will only be valid in the PREROUTING and OUTPUT chains. More info about these targets can be found in the iptables and iptables-extensions man pages.
Rules
Delete all rules:
Set a default policy:
Set a rule for a certain protocol:
Iptables extensions
iptables can use extended packet matching and target modules using the -m option.
If a protocol is specified using the -p option, and an unknown extension option is encountered, iptables will load a match module identical to the name of the protocol.
These extended match modules allow further constraints on rules and add more command line options.
Matching the state of a packet
Redirecting a packet destined for port 80 to a different ip:
View man iptables-extensions for more information.
Snort
You can write rules for snort by creating a .rules file in the /etc/snort/rules folder. Alternatively, you can edit the snort.conf file or use the local.rules file. Read more about how to write snort ruleshere.
The complete docs can be foundright here.
Basic snort rule syntax:
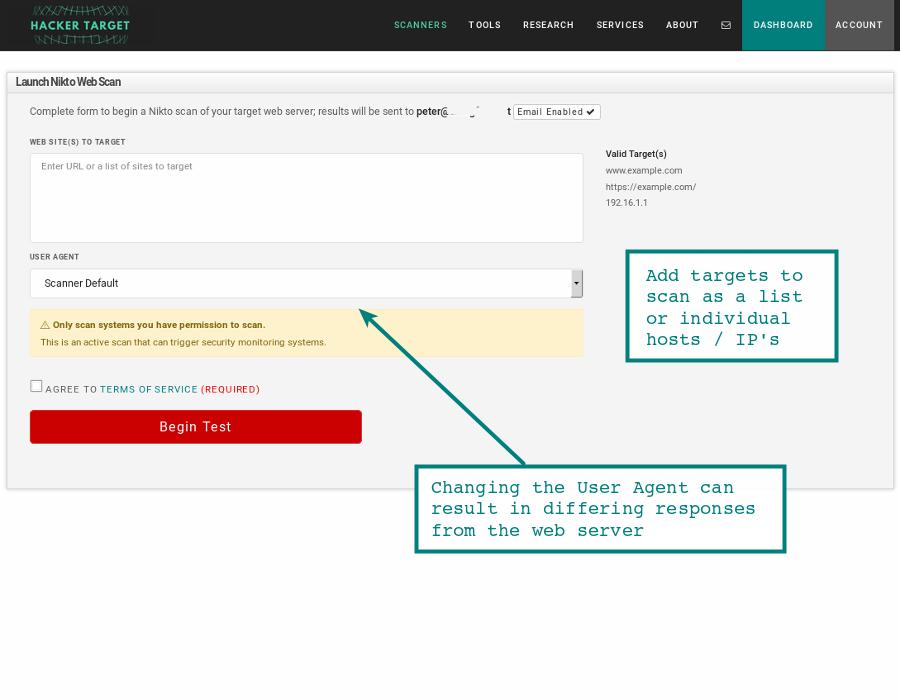
Nikto Cheat Sheet
Actions
- alert: alerts and logs the packet when triggered
- log: only logs the packet when triggered
- pass: ignored or drops the packet or traffic matching
- dynamic: alerts then activates a dynamic rule or rules
- drop: block and log the packet
- reject: block the packet, log it, and then send an unreachable message
- sdrop: block the packet but do not log it
Rule options
- msg: <sample message>: Logs the message into
/var/snort/logon a successful match - flags: <flags>: Match specific TCP flags (see below)
- content: <text>: Match specific text in a packet
- content: |<hex>|: Match specific hex characters
- sid: <snort id>: Unique number to identify rules easily
- rev: <revision #>: Rule revision number
- reference: <ref>: Where to go to get more info about the rule
- gid: <generator id>: Identifies which part of
snortgenerated the alert.
You can find more information about rule optionsat the snort docs.
TCP flags
- A = ACK
- F = FIN
- P = PSH
- R = RST
- S = SYN
- U = URG
- 2 = reserved bit
- 1 = most significant bit
- 0 = no flags
Examples
Alert when a URL is over 200 bytes long.
Web Penetration Testing
Resources
Web Penetration Writeup:A pen-test walk-through, eerily mirroring the web penetration testing practical.
SQL Injection Cheat Sheet:The SQL injection cheat sheet used in the aforementioned walkthrough.
nmap Cheat Sheet:Simple
nmapcheat sheet. The commandman nmapis also very useful.
- nikto Cheat Sheet:Nikto scanner cheat sheet.
man niktocan also be used on Kali.
- sqlmap Cheat SheetSqlmap scanner cheat sheet.
man sqlmapcan also be used on Kali.
Steps
Identify the devices by performing a ping scan.
After finding the devices, perform a service / port scan for each device.
Since this is a web penetration test, use the results of the previous
nmapscan to find which device is running ahttporssl/httpservice. These are typically on ports80,433or8080and contain words likehttpd,Apache, etc.When the target device has been identified, visit the pages in a web browser to see what’s there. Alternatively, this could be done with the
curlcommand. Check for common directories and files like/login,sitemap.xmlandrobots.txt.If nothing in particular stands out from an initial inspection, use the
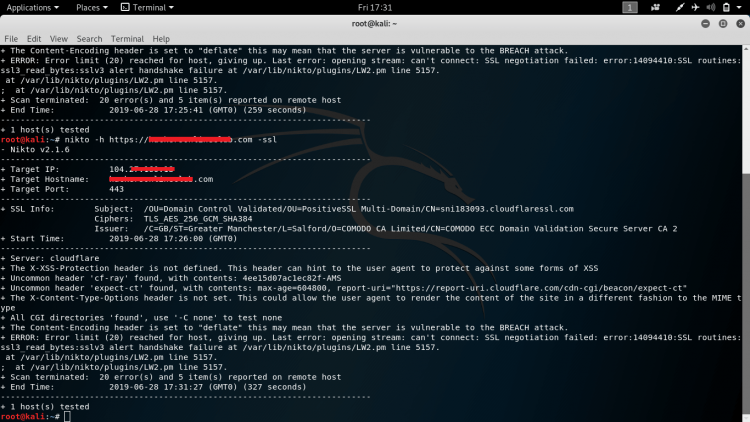
niktocommand to perform a more thorough inspection.If nothing useful pops up, run
niktoon a different port or using ssl.It might also pay to run
niktowith different tuning options. To focus on SQL Injection use the commandFor more help with
nikto, refer tonikto -horman nikto.Note: Nikto is self described as being not stealthy, if stealth is your goal it may pay to spend more time on Step 4.
Nikto will return a bunch of information relating to your query. Most likely you’ll see a bunch of directories and files on the server that may be of interest. You should inspect these files and look for any SQL injection opportunities.
Plan in advance how you intend to get a reverse shell, as the exam has a fixed time and
sqlmapcan take a long time to run. In the case of the practical, it was obvious that it would be through the wordpress site. Once I’d gathered enough information, I decided that the easiest way to get into the wordpress site would be finding an admin user’s password.
Attack
When a page with a form or endpoint that is vulnerable to SQL injection is found, use the sqlmap tool to perform an attack.
If you’ve found a form, you can paste the following JavaScript method into your browser’s console to get the data string.
When you have it, try and find a list of databases using:
Typically, it will use a delay based technique to determine the contents of the SQL database. If you issued the above command, and followed the prompts, you’ll see the command will slowly letter-by-letter spell out the databases on the device. When you see one that will aid your takeover.
Once you see a database that will be of interest, feel free to perform a keyboard interrupt and continue on with the next steps.
Find the tables in the target database:
Once again it will type out letter-by-letter the contents of the table. When you spot something interesting, skip straight to finding it’s contents.
Find the contents of a table:
Note: Instead of going through step by step like I explained, you could use the sqlmap wizard. I find this to be incredibly slow however, and wouldn’t encourage it in a time-limited situation. Nonetheless, if you’d like to use the wizard issue the command:
Take control
The steps to get a reverse shell will depend on the content of the database. In the case of the practical, finding the contents of the database allowed you to log into the wordpress site that was present. After logging in, a php reverse shell script could easily be added to the site.
Tips

Nikto Cheat Sheet
Try accessing the site using different protocols.
https://andhttp://are often used to show different things.sqlmapcan often take ages, but it stores data to disk as it goes. So if you perform a keyboard interrupt you can often get right back to where you were.The default table name for a Wordpress site is
wordpress8080The Wordpress admin page lives as
/adminThis gistshows an easy way to get a reverse PHP shell
Before visiting the page, you should set up the listener.
Since the
POSTmethod doesn’t show the data as query parameters, you will have to use the--dataoption ofsqlmap. More information on usingsqlmapwithPOSTcan be foundhere.John the Ripper is a useful piece of software in Kali that can crack passwords.
Exploiting Buffer Overflows
Resources
Before attempting a buffer overflow, you should read up on how the CPU works on a low level.
Steps
Setup the machine with the vulnerability and open Immunity Debugger.
Attach Immunity Debugger to the application and start it up.
Determine how to cause the buffer overflow - you will most likely be told. When you know, you can start to fuzz the input to cause a crash. The following script was used for SLMail and comes fromhere.
Upon causing a crash, note down the length of the buffer required to cause the crash.
Determine what part of the message ends up being written to the EIP register. This can be done using the
pattern_create.rbfile in the metasploit tools directory. This will create a unique string that will allow you to see how many characters are required to make it into the program counter.Now copy and paste this into your python script.
Finally, inspect immunity debugger and note the characters in the EIP register. Cross reference with the pasted buffer to determine the offset.
Note:
pattern_create.rbhas a sister tool calledpattern_offset.rbthat can help you to determine the offset.
Now that you know start of the part of the message that overflows into the program counter, verify that it’s correct by sending a buffer made of “A's, “B's and “C's. The “A's represent the data that consumes the stack, the “B's represent the return address and the “C's represent the arbitrary shellcode to be executed.
You can easily create this buffer using python:
Once you’ve verified that the offset is correct, you have to find a way to get an instruction into the program counter that will jump to the top of the stack and begin executing your arbitrary shell code.
Inside immunity debugger, click on the command box at the bottom of the page and write the following command:
This will bring up a list of modules / libraries that are dynamically linked to the executable. Inside one of these modules is probably the assembly command
JMP ESP, which will jump to the top of the stack.When deciding on a DLL to use, it’s important that you choose one that was compiled with DEP (Data Execution Prevention) and ASLR (Address Space Layout Randomization) disabled.
Once you’ve found a module with the previous security features turned off, you must search for the command
JMP ESPinside it. The shellcode for this command isFFE4which can be found using thenasm-shell.rbutility in metasploit. Return to the command box and issue:Note down the address of the memory that contains the command. As Windows is little endian, the bytes of the address should be reversed.
There’s one final thing to do before starting the attack - find “bad characters” that will cause your program to stop.
To find out what characters are bad, send a list of all ascii characters and note where it stops. Remove the troublesome characters and try again until all of them make it through. Make note of the “bad characters”.
Here’s a list of all ascii characters:
Attack
Now that you’ve got all the information required to execute code on the target machine. This can be done using the tools msfvenom and shikata_ga_nai.
Once you have the payload, add it back into your python code. It’s important that you space the payload out with some NOP characters (x90) so that your program has space to execute.
Take control
Nikto Cheat Sheet 2020
Now that you’ve got your payload ready, it’s just a matter of setting up a nc listener and performing the exploit. It’s important that you test the payload before attacking a real machine, because you only get one shot. It’s also important that you don’t forget to make the return address the right one for the network you’re on.
Nikto Cheat Sheet Sans
Changing from X.org and i3wm to Sway and Wayland

How to complete the Advent of Code 2018 challenges with Rust